Facebook Messenger Phishing: Vietnamese Hackers’ Python-Based Scheme
Vietnamese Hackers Employ Python-Based Stealer via Facebook Messenger
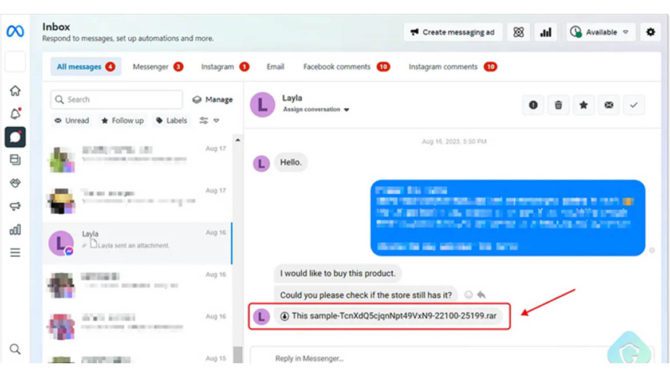
In an ingenious phishing maneuver, malevolent actors are harnessing Facebook Messenger as a conduit for disseminating messages that harbor malicious attachments. These messages emanate from a multitude of counterfeit and commandeered personal accounts, all part of a coordinated effort aimed at assuming control over the targets’ business accounts.
Once again, this stratagem can be traced back to a Vietnamese-based faction. This campaign employs a diminutive, compressed file attachment, concealing a potent Python-based data extractor. The deployment of this extractor unfolds in a multi-stage process, enriched with deceptively straightforward yet highly effective obfuscation techniques, as elucidated by Guardio Labs researcher Oleg Zaytsev in an analysis released recently.
In the context of these offensive maneuvers, christened “MrTonyScam,” prospective victims receive enticing messages, luring them into interacting with the RAR and ZIP archive attachments. This interaction triggers the deployment of a dropper, which subsequently retrieves the next stage from either a GitHub or GitLab repository.
Python-Based Data Extractor: Vietnamese Hackers’ Deceptive Tactics
This payload, in itself, is yet another archive file, housing a CMD file. Within this CMD file lies a concealed Python-based data extractor, obfuscated to surreptitiously siphon away all cookies and login credentials from diverse web browsers. These ill-gotten gains are then routed to an endpoint under the control of the malefactors, either via Telegram or Discord API.
One particularly astute stratagem employed by the adversaries involves the deletion of all pilfered cookies post-extraction. This tactical move effectively logs victims out of their own accounts. Subsequently, the scammers exploit the purloined cookies to change passwords and wrest control of the compromised accounts.
The link between the threat actors and Vietnam is established through the presence of Vietnamese language references in the Python-based data extractor’s source code, along with the inclusion of Cốc Cốc, a Chromium-based browser popular in the country.
Despite the fact that triggering the infection necessitates user interaction to download, unzip, and execute the attachment, Guardio Labs has observed a notable success rate. Over the past month alone, an estimated 1 in every 250 individuals who interacted with these messages fell victim to the attack.
The majority of these breaches have been reported in countries including the United States, Australia, Canada, France, Germany, Indonesia, Japan, Nepal, Spain, the Philippines, and Vietnam, among others.
Oleg Zaytsev aptly points out, “Facebook accounts with a strong reputation, high seller ratings, and a substantial following can be lucratively exploited on the clandestine markets. These accounts serve as conduits for reaching a wide-ranging audience for the dissemination of advertisements and, unfortunately, further scams.”
This disclosure follows closely on the heels of revelations by WithSecure and Zscaler ThreatLabz regarding the newly unveiled Ducktail and Duckport campaigns. These campaigns employ malevolent posting tactics to target Meta Business and Facebook accounts.
The prevalence of Vietnamese-centric elements in these threats and the striking convergence in terms of capabilities, infrastructure, and victim profiles imply collaborative relationships between disparate threat actors. They may share tools and tactics across these threat groups or participate in a fragmented, service-oriented Vietnamese cybercriminal ecosystem, analogous to a ransomware-as-a-service model, with a focal point on social media platforms such as Facebook, as highlighted by WithSecure.
Stay Updated about the latest technological developments and reviews by following TechTalk, and connect with us on Twitter, Facebook, Google News, and Instagram. For our newest video content, subscribe to our YouTube channel.